最近的

This paper describes the use of the LaTeX qjrms4.cls class file for setting papers for the Quarterly Journal of the Royal Meteorological Society

Gene regulatory networks have an important role to study the behaviour of genes. By analysing these Gene Regulatory Networks we can get the detailed information i.e. the occurrence of diseases by changing behaviour of GRNs. Many different approaches are used (i.e. qualitative modelling and hybrid modelling) and various tools (i.e. GenoTech, GINsim) have been developed to model and simulate gene regulatory networks. GenoTech allows the user to specify a GRN on Graphical User Interface (GUI) according to the asynchronous multivalued logical functions of René Thomas, and to simulate and/or analyse its qualitative dynamical behaviour. René Thomas discrete modelling of gene regulatory network (GRN) is a well known approach to study the dynamics of genes. It deals with some parameters which reflect the possible targets of trajectories. Those parameters are priory unknown. These unknown parameters are fetched using another model checking tool SMBioNet. SMBioNet produces all the possible parameters satisfying the given Computational Logic Tree (CTL) formula as input. This approach involving logical parameters and conditions also known as qualitative modelling of GRN. However, this approach neglects the time delays for a gene to pass from one level of expression to another one i.e. inhibition to activation and vice versa. To find out these time delays, another modelling tool HyTech is used to perform hybrid modelling of GRN. We have developed a Java based tool called GenNet http://asanian.com/gennet to facilitate the model checking user by providing a unique GUI layout for both qualitative and quantitative modelling of GRNs. As we discussed, three separate modelling tools are used for complete modelling and analysis of a GRN. This process is much lengthy and takes too much time. GenNet assists the modelling users by providing some extra features i.e. CTL editor, parameters filtering and input/output files management. GenNet takes a GRN network as input and does all the rest of computations i.e. CTL verification, K-parameters generation, parameter implication to GRN, state graph, hybrid modelling and parameter filtration automatically. GenNet serves the user by computing the results within seconds that were taking hours and days of manual computation

El barómetro es un instrumento de medición atmosérica, específicamente utilizado en la determinación de la fuerza por unidad de superficie ejercida por el peso de la atmósfera. Existe un gran número de equipos atmoféricos con distintos tipos de estos aparátos y son diariamente utilizados ya que la presión atmosférica juega un papel importante en la determinación y pronóstico del tiempo así como en el área de investigación al momento de realizarse experimentos ya que pueden llegar a afectar o hacer variar el funcionamiento de muchos aparatos electrónicos y mecánicos.
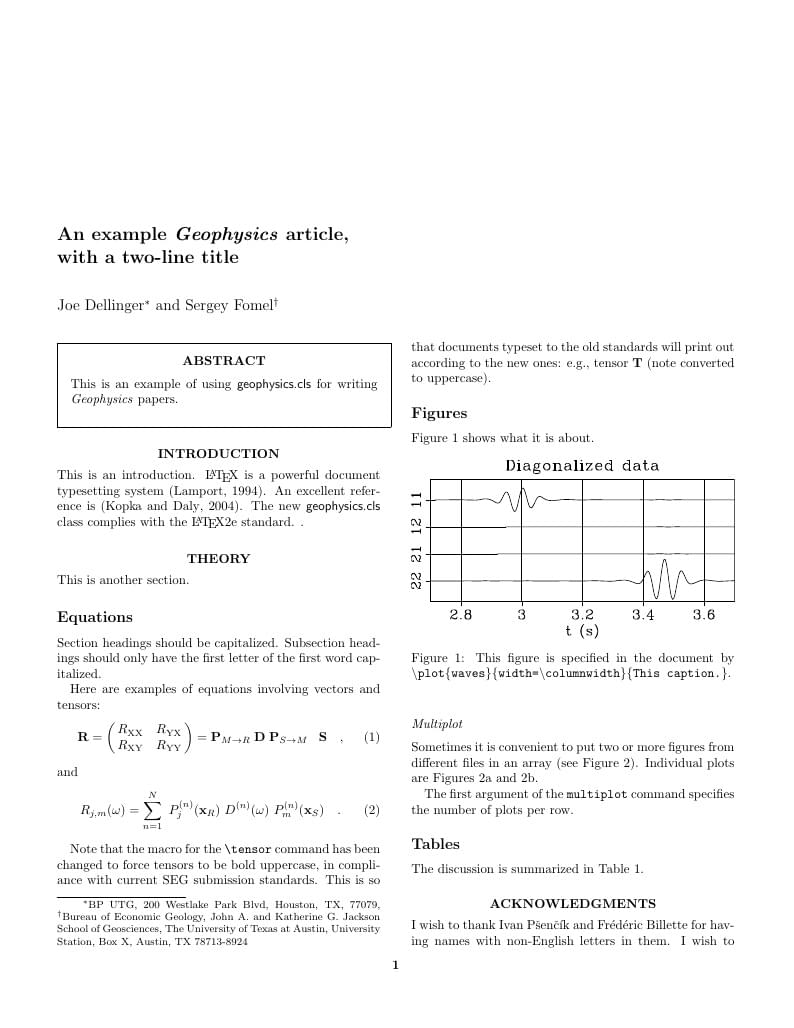
This is an example of using geophysics.cls for writing two-column Geophysics papers.

This is a template to perform an article to International Conference on Pattern Recognition systems (ICPRS) Update dates.

Submitted full papers are to be supposed to be of at least 4 pages length. The authors should submit their papers electronically, written in English, due to the given deadline, through a web upload procedure available, see http://ifsa-eusflat2021.eu/.
![The AAAI 2023 Workshop on Representation Learning for Responsible Human-Centric AI [Template]](https://writelatex.s3.amazonaws.com/published_ver/27233.jpeg?X-Amz-Expires=14400&X-Amz-Date=20260218T131305Z&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAWJBOALPNFPV7PVH5/20260218/us-east-1/s3/aws4_request&X-Amz-SignedHeaders=host&X-Amz-Signature=4569a51c2617e393398ee2bfbeef2ee0dfdb2c8ddddcfcaddec9779dabf8cb40)
This is the template for camera-ready submissions to the AAAI 2023 Workshop on Representation Learning for Responsible Human-Centric AI (R2HCAI).

Updated template for USENIX conferences with style file exits dating 2020.

Modelo de escrita de Trabalho de Conclusão de Curso para MBA em Gestão Empresarial em Ambiente Tecnológico